Woke up this morning and found two emails from domaincorp.org in my Inbox stating my domains are being used for spamming and spreading malwares recently. Subject line contained “Domain Abuse Notice” which looked serious.
I mean WOHA! I do write about ‘stuff’ but doesn’t mean I send out emails to anyone. I don’t even respond to my emails half the time cause I don’t really need another SEO expert, another advertiser, another promoter or a globally acclaimed graphics designer to design ‘tings’!
But then again, you read about all these reports that explains how malware and virus’s are served via Advertisement etc. So I decided to carefully examine the email and it’s contents in an attempt to find out more information. Before I even opened the actual email, I checked it’s header and Domain Whois. I always do this, specially Whois because you are unlikely to receive an abuse notice email from any domain that was registered few weeks back. Most abuse notice emails are served by large organizations and domains that has been around for years and built enough reputation for everyone to take them seriously.
Whois information
I checked their whois from https://who.is/whois/domaincop.org
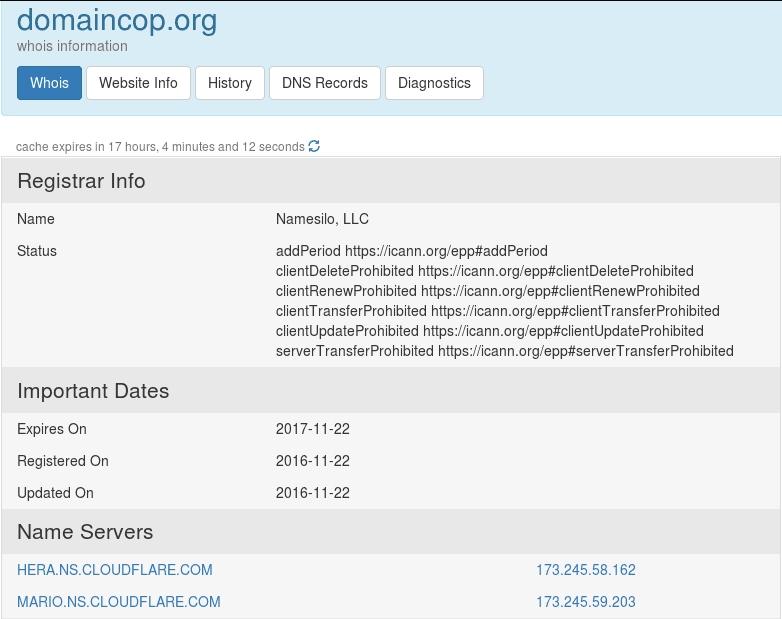
Nice, Registered On 2016-11-22, Updated On 2016-11-22 and today is 2016-11-23. I mean duh, it’s still 22nd of November is some parts of the world. They also has PrivacyGuard enabled which means you cannot see the real owners name or details like darodar.com referrer spam.
Inspect URL and it’s content
The next obvious thing was to check the URL that was sent to me to view the abuse my domains has inflicted. erm, do I use a browser? Perhaps not, I decided to use cURL.
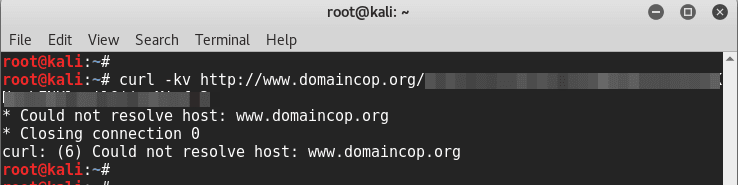
hang on, the domain seems to have no DNS response. Let’s double-check that with dig command
dig returned NXDOMAIN response which means the domain doesn’t exists. It seems either they’ve disabled their domain and/or Cloudflarebanned/removed them. In any case, there is no way to inspect that URL for me now. ‘sad panda’
Sample email
Here’s one of emails I received from “Imogen Murray” <imogen_murray@domaincop.org>; (the other email was from “Isaac Wright” <isaac-wright@domaincop.org>; ) with exactly same content:
Conclusion
Not sure what this email was about, but in case you ever get these type of emails, here’s what you always do:
- Check Domain Whois
- Check the URL without actually going into it (cURL it)
- Use online scanners to check the links
- Check dig/nslookup info
- Search in Google
- If you must visit the URL, do it from a command line tool or from a VM.
In short, you are unlikely to get such emails from multiple senders from a domain that was setup yesterday, got banned today and has people around the world talking about it being a scam. Another way is to check spammy links is by using reputed providers online site review tools. Here’s a list of them:
Real Time Scanners:
- Comodo Web Inspector: Examines the URL in real-time
- Joe Sandbox URL Analyzer: Examines the URL in real time
- Is It Hacked: Performs several of its own checks of the URL in real time and consults some blacklists
- IsItPhishing: Assesses the specified URL in real-time
- Sucuri SiteCheck: Scans the URL for malware in real time and looks it up in several blacklists
- Zscaler Zulu URL Risk Analyzer: Examines the URL using real-time and historical techniques
Historical Reputation data:
- AVG Website Safety Reports: Provides historical reputation data about the site
- Blue Coat WebPulse Site Review: Looks up the website in BlueCoat’s database
- BrightCloud URL/IP Lookup: Presents historical reputation data about the website
- Cisco SenderBase: Presents historical reputation data about the website
- Cymon: Presents data from various threat intel feeds
- Deepviz: Offers historical threat intel data about IPs, domains, etc.
- FortiGuard lookup: Displays the URL’s history and category
- IBM X-Force Exchange: Provides historical data about IPs, URLs, etc.
- Intel/McAfee: : Presents historical reputation data about the website
- KnownSec: Presents historical reputation data about the website; Chinese language only
- PhishTank: Looks up the URL in its database of known phishing websites
- Malware Domain List: Looks up recently-reported malicious websites
- MalwareURL: Looks up the URL in its historical list of malicious websites
- McAfee Site Advisor: Presents historical reputation data about the website
- MxToolbox: Queries multiple reputational sources for information about the IP or domain
- Norton Safe Web: Presents historical reputation data about the website
- Open Threat Exchange: Presents diverse threat intelligence data from AlienVault
- PassiveTotal: Presents passive DNS and other threat intelligence data
- Quttera ThreatSign: Scans the specified URL for the presence of malware
- Reputation Authority: Shows reputational data on specified domain or IP address
- Trend Micro: Presents historical reputation data about the website
- Unmask Parasites: Looks up the URL in the Google Safe Browsing database
- URL Blacklist: Looks up the URL in its database of suspicious sites
- URL Query: Looks up the URL in its database of suspicious sites and examines the site’s content
- URLVoid and IPVoid: Looks up the URL or IP in several blacklisting services
- VirusTotal: Looks up the URL in several databases of malicious sites
- vURL: Retrieves and displays the source code of the page; looks up its status in several blocklists
- ThreatMiner: Presents diverse threat intelligence data
These are industry leaders for checking and categorizing Domains/URL’s and marking them accordingly. For new domains, use the Live scanners; for older domains, use the historical reputation scanners. In any case, stay safe and happy browsing.



